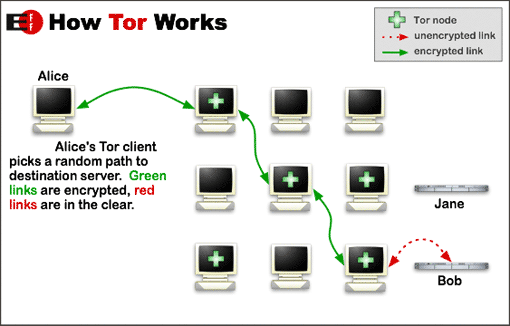
I make you aware of their solution and ask if you get
if it is secure or not.
The woman innovator has worked on it for 8 years
and she have been granted patents in several countries.
She describe ho wit works on her companies home page.
http://www.kelisec.com/index.php/method
read the rest of the explanation using the link.I. A initiates a session by connecting to the access server (AS).
The server then authenticates A.
If A is a Kelisec member the AS initiates communication with B
which also will be authenticated in a similar process.
Each node has a unique DNA. The two unique elements are blended
in the AS. The blended DNA is irreversible. A secure session
has been established.
Now the good thing is secure authentication that the Sender of data
is the one they pretend to be
do the authentication.
Now the very bad thing is that none will be able to be anonymous
anymore if this is by law implemented on ISP level.
Each computer has to have this feature for to be sold and used.
Each motherboard.
Sure this is my pessimistic view on the kind of society
we are heading towards. A total "1984" kind of absolute
knowledge on every thing the user of computers and smartphones
do online. Whom you are and whom you contact and where you
where when contact got established. What page on internet you
look on and download and so on.
Sure the good thing is they hopefully catch some Robber that
exchange plans with his buddies or a some other mean spirited
action someone want to take.
But the bad effect can be total knowledge of each individual
We will have no freedom to disagree anymore.